On 13th October 2025 at 16:22 UTC+2 I opened one of my websites, dev.chris-besch.com, and found it hacked (see the below screenshot).
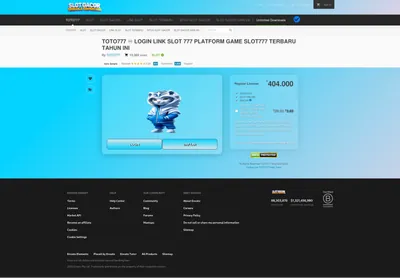
Let me explain what happened and how I resolved the situation. Firstly, I'm using GitHub Pages to host the website in question. GitHub Pages allows me to define what domain to host the website on.
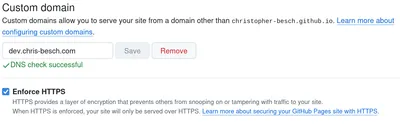
How does that work?
After all GitHub doesn't have control over my domain, only I do.
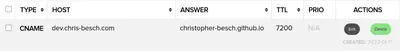
GitHub asks me to forward dev.chris-besch.com to christopher-besch.github.io, which is under their control.
I do so with a DNS record using the domain registrar of my choice.
There's no way around doing this and I never thought much of it, until the other day.
That other day when someone else apparently got control over my domain.
What Happened?
A few days ago I accidentally deleted the git branch GitHub Pages feeds on. Although I recreated the branch shortly after and unbeknown to me, that permanently disabled my GitHub Pages deployment. Therefore, my domain forwarded to GitHub's infrastructure but wasn't used by any GitHub Page anymore. Someone realized that and chose the domain for their malicious website. Luckily I realized the malicious website fairly quickly. Furthermore, I only use that domain for debugging purposes, anyways. Still, this means people are constantly scanning for domains that point to GitHub's infrastructure but aren't used by any GitHub Page. That's scary.
Another scary thing is the valid SSL certificate the attacker received for my domain. She used the domain validation of GitHub's Let's Encrypt certificate. Those are easy to get once she had control over my domain. An organization or extended validation wouldn't be possible here. Those kinds of validations proof that a website has a right to be where it is; this situation shows that. Still, browsers don't really differentiate between the validation types in the user interface.
Resolution
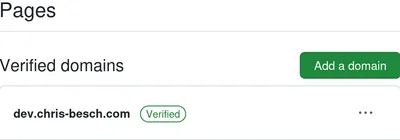
I didn't forward to a generic GitHub domain, I forwarded to christopher-besch.github.io.
So, GitHub could have checked my DNS record and realized that I, christopher-besch, don't want someone else hosting GitHub Pages on my domain.
Though, GitHub doesn't do that.
Instead, it needs a specific TXT DNS record to understand that that's my domain.
They call this feature "verified domains".
I enabled that and got my domain back.
Conclusion
This was a lesson for me. By pointing my domain at someone else's infrastructure I put trust in that someone else. And in this situation GitHub broke that trust. Whenever you're forwarding to infrastructure you don't directly control, you're trusting them. Every DNS forward, every web link, foreign IP address is an expression of trust in foreign infrastructure. Be aware of that.
Similar Articles
The History of Forgejo's Pub-Sub Pattern
10min Thursday, 30th October, 2025
I created a tool to visualize Forgejo's Pub-Sub pattern. Why not run that tool on all 24 thousand commits in Forgejo's history? What could possibly go wrong?
Forgejo Actions Notification Development
17min Thursday, 20th November, 2025
Some stories of how I work on Forgejo. How is a Go project structured? What's the point of Forgejo's layered architecture and what's that pub-sub pattern? Additionally, I exhaustively explain how to setup a development environment for Forgejo.

When You Don't Take the Shot
2min Wednesday, 10th December, 2025
I list the things I realized to improve my photos. There are the technical abilities (equipment, exposure, post processing, ...) and the surrounding conditions (time, location, ...). And sometimes, photography means letting the shutter rest.

Why I love Open-Source
23min Saturday, 11th October, 2025
We all live in a world of immensely complex technology. The concept of Open-Source might seem radical at first but it's indispensable in our world. Regardless if you are a user, developer or simply interested in a healthy society, you benefit from Open-Source and we should fight for every bit of it. Open-Source is a quality mark, a form of democracy and ownership, capitalism at its best and thus the response to this world, a world in which software exists. This article gets to that conclusion without requiring any prior technical knowledge.

